Echooo
✅ picoCTF 2018: 300 Points
📄 echo.c: source
Challenge:
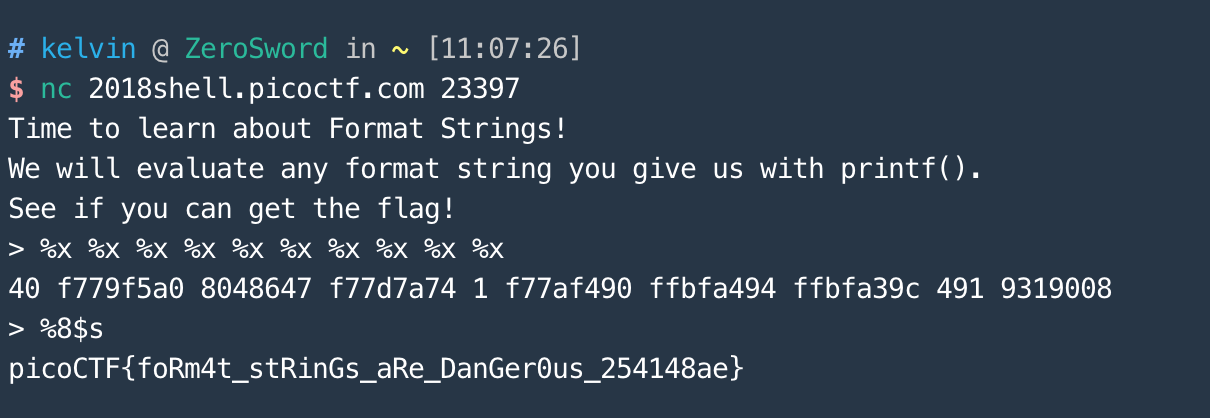
This program prints any input you give it. Can you leak the flag? Connect with nc 2018shell.picoctf.com 23397By reading the source code (i.e. echo.c), we know the program will use fgets to read user input and use printf to print it out.
However, there is a vulnerability exposed here which could be exploited using format string attack. First, we need to know how function is being called in C. Generally speaking, the argument(s) of a function call will be pushed onto the stack and popped from the stack later. Let's take an example of printf("%d %d\n", 1, 2)
Back to echo.c, What would happen if we entered "%x"? The function call printf(buf) would become printf("%x") and most importantly printf expects the argument is already on the stack and therefore it pops. In this case, we can use %x to try to get the address of flag_ptr (i.e. the 8th hexadecimal after attempts). Lastly, use %8$s to print the string using the address of flag_ptr.