Assembly-0
✅ picoCTF 2018: 150 Points
Challenge:
What does asm0(0x2a,0x4f) return? Submit the flag as a hexadecimal value (starting with '0x'). NOTE: Your submission for this question will NOT be in the normal flag format. Source located in the directory at /problems/assembly-0_3_b7d6c21be1cefd3e53335a66e7815307.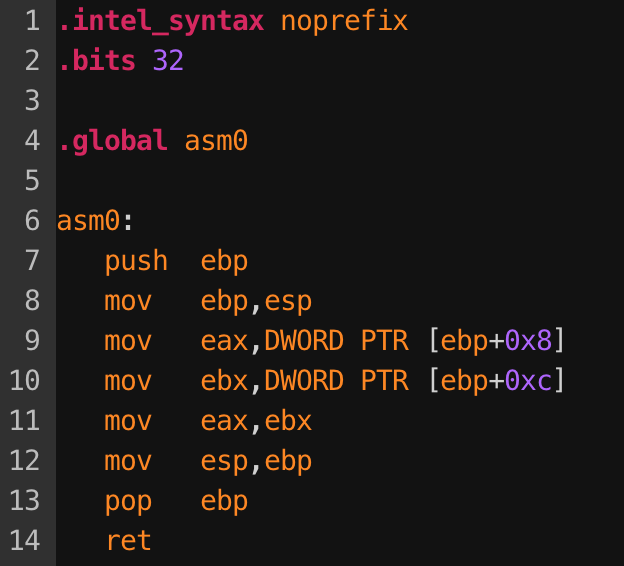
This challenge is a simple one, as you just need to try two answers - either 0x2a or 0x4f. But it is always good to know the reason behind the scene. Let's have a look at the "stack" below.
This is how the stack looks like after line 8 (i.e. mov ebp, esp) is executed. What line 9 and 10 are doing is to dereference the addresses (ebp+0x8) and (ebp+0xc) (where the 1st and 2nd arguments are). Copy those two values into eax and ebx respectively.
At this stage, eax is holding 0x2a and ebx is holding 0x4f. Line 11 is the key of this challenge as it copies the value of ebx to eax, so now eax = ebx = 0x4f. In convention, eax is used for return value of a function call. Back to the question, what asm(0x2a, 0x4f) returns is the 2nd argument, which is 0x4f (i.e. the flag)